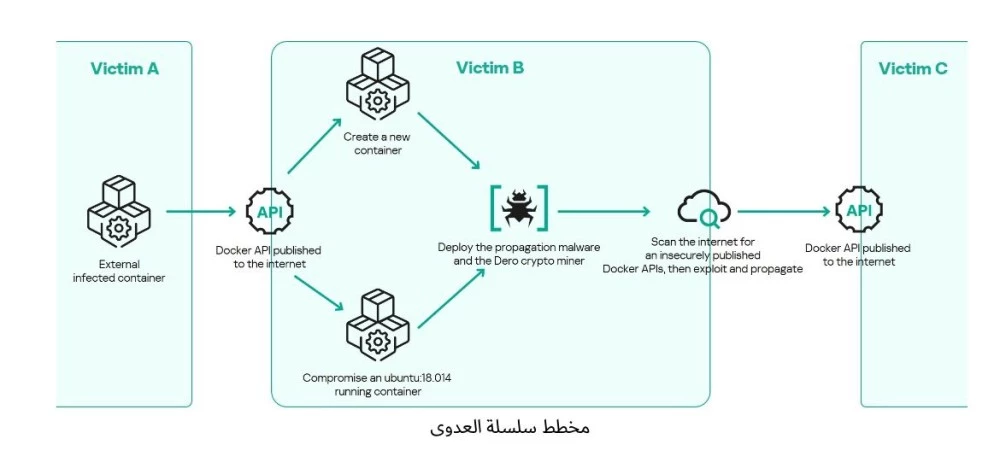
Kaspersky Security Services experts have identified a sophisticated cyberattack campaign targeting containerized environments to deploy a miner for the Dero cryptocurrency. The attackers abuse exposed Docker APIs — parts of Docker, an open-source container development platform.
In 2025, there are nearly 500 insecurely published Docker API default ports worldwide on average each month. In this campaign, cybercriminals inject two types of malware:
- The miner itself
- A propagation malware that spreads the campaign to other vulnerable container networks
Campaign Discovery and Impact
Kaspersky discovered the campaign during a compromise assessment project. Organizations using containerized infrastructure with unprotected Docker APIs are at risk — including:
- Tech companies
- Software developers
- Hosting & cloud service providers
According to Shodan, there are 485 exposed Docker API ports/month, creating a large attack surface.
Attack Methodology
Once an exposed API is found, attackers either:
- Compromise existing containers, or
- Deploy new malicious containers based on standard Ubuntu images
Two malwares are injected:
- “cloud”: a Dero miner
- “nginx”: maintains persistence, ensures execution, and scans for other exposed environments
These operate without C2 servers, making each infected container an independent threat scanner.
Expert Insight
“Each compromised container can launch new attacks. Without urgent protection, infections could grow exponentially,”
explains Amged Wageh, Incident Response & Compromise Assessment expert at Kaspersky.“Containers are core to development and scalability. Their widespread use across cloud-native, DevOps, and microservices makes them attractive to attackers. A 360-degree security approach is now a must.”
Masquerading Technique
The malware names “nginx” and “cloud” are embedded in binaries — a common tactic to pose as legitimate tools and evade detection.
Kaspersky Recommendations
- Do not expose Docker APIs unless operationally necessary
- Use TLS to secure exposed APIs
- Conduct Compromise Assessments regularly
- Use Kaspersky Container Security to protect the full container lifecycle
- Adopt Managed Security Services like:
- Compromise Assessment
- Managed Detection & Response (MDR)
- Incident Response
Detection & Technical Analysis
Kaspersky detects the malware as:
Trojan.Linux.Agent.genRiskTool.Linux.Miner.gen
Full technical report: Securelist















